Microsoft is strengthening Windows' security by adding a very important rule to its antivirus. A new ASR rule is being introduced to Microsoft Defender.
Before we get into it, let's talk about a method that hackers can use to steal a user's Windows password.
What is LSASS?
You may have noticed LSASS.exe in your Task Manager, it is related to a process called Local Authority Server Service. LSASS authenticates users who log on to a computer, and is protected by Microsoft Defender's Credential Guard. The issue with it is that Credential Guard is not compatible with all programs, e.g. custom smartcard drivers. So, it is not implemented in all environments.
When an attacker has breached a user's computer, they can easily gain access to the LSASS process via special tools like Mimikatz. The resultant file created by the tool, is a memory dump that contains the passwords and usernames of the users who were logged in to the system.
The passwords are displayed in plain-text, thus allowing the attacker to gain full access to the operating system. And all this can be done remotely, and Microsoft Defender will not block access to it because LSASS is a legitimate process and its memory dump is not harmful. It can only detect programs that are maliciously accessing the process, but can't prevent the memory dump from being created, or transmitted to steal the user's credentials.
That's pretty scary, isn't it.
Microsoft Defender gets an Attack Surface Reduction rule
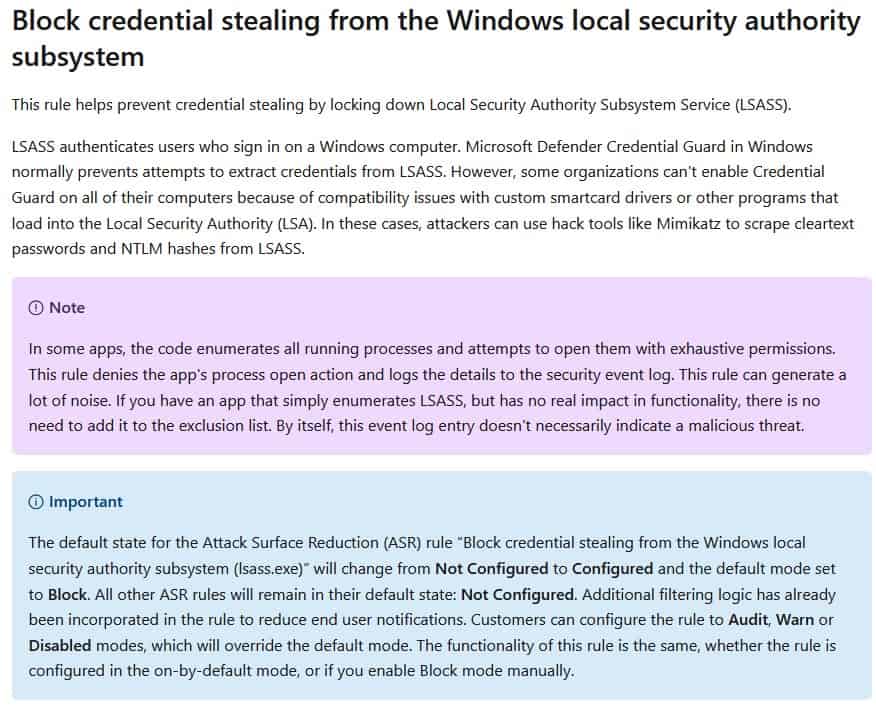
The solution to this security issue is quite simple, protect LSASS from unauthorized access, and this whole mess can be avoided, right? That is precisely what the Redmond company is doing, by adding a new rule called Attack Surface Reduction (ASR). This rule will block programs from opening LSASS and in turn also prevents them from creating the memory dump. It will block access to LSASS even if a program that has elevated rights, i.e., administrator privileges, tries to open the process.
It gets better, according to Microsoft's documentation, this ASR rule will be enabled by default, while all other rules related to it will remain in their default state "Not Configured".
Is ASR a good solution? Well, if you're Microsoft Defender, this does look promising. It is not completely fool-proof though, but what is. We have to remember that malware are also evolving, and becoming complex year-after-year.
On the other hand, if you are using a third-party antivirus on your computer, the ASR rule is disabled. So, that makes the LSASS vulnerable again. Bleeping Computer reports that the ASR rule has already been bypassed by some security researchers, who exploited Microsoft Defender's exclusion paths. The exclusions apply to all ASR rules, and since this LSASS access falls in the same category, it makes it possible for hackers to bypass the restrictions. The report mentions that users running on Windows Enterprise, Windows 10 Pro and Windows 11 Pro will be protected by the new ASR rule.
That said, the new ASR rule has been welcomed by security researchers, as it makes Windows a little more secure, and that's always welcome as it will result in fewer stolen passwords.
On a side note, Microsoft Defender Preview is a new dashboard that lets you manage the security of your devices.
Thank you for being a Ghacks reader. The post Microsoft Defender gets better at preventing Windows passwords from being stolen appeared first on gHacks Technology News.
0 Commentaires