Microsoft unveiled plans in July 2022 to roll out brute force protection against local accounts in the next version of Windows 11 and Windows Server 2022. The added protection is now enabled on new machines running Windows 11 and on "any new machines that include the October 11, 2022 Windows cumulative updates before the initial setup".
In other words, local accounts on new machines are protected automatically against brute force attacks. Local accounts on old machines are not protected, even if the October security updates are installed on these machines. Administrators may enable these protections, provided that they have access to the Group Policy editor.
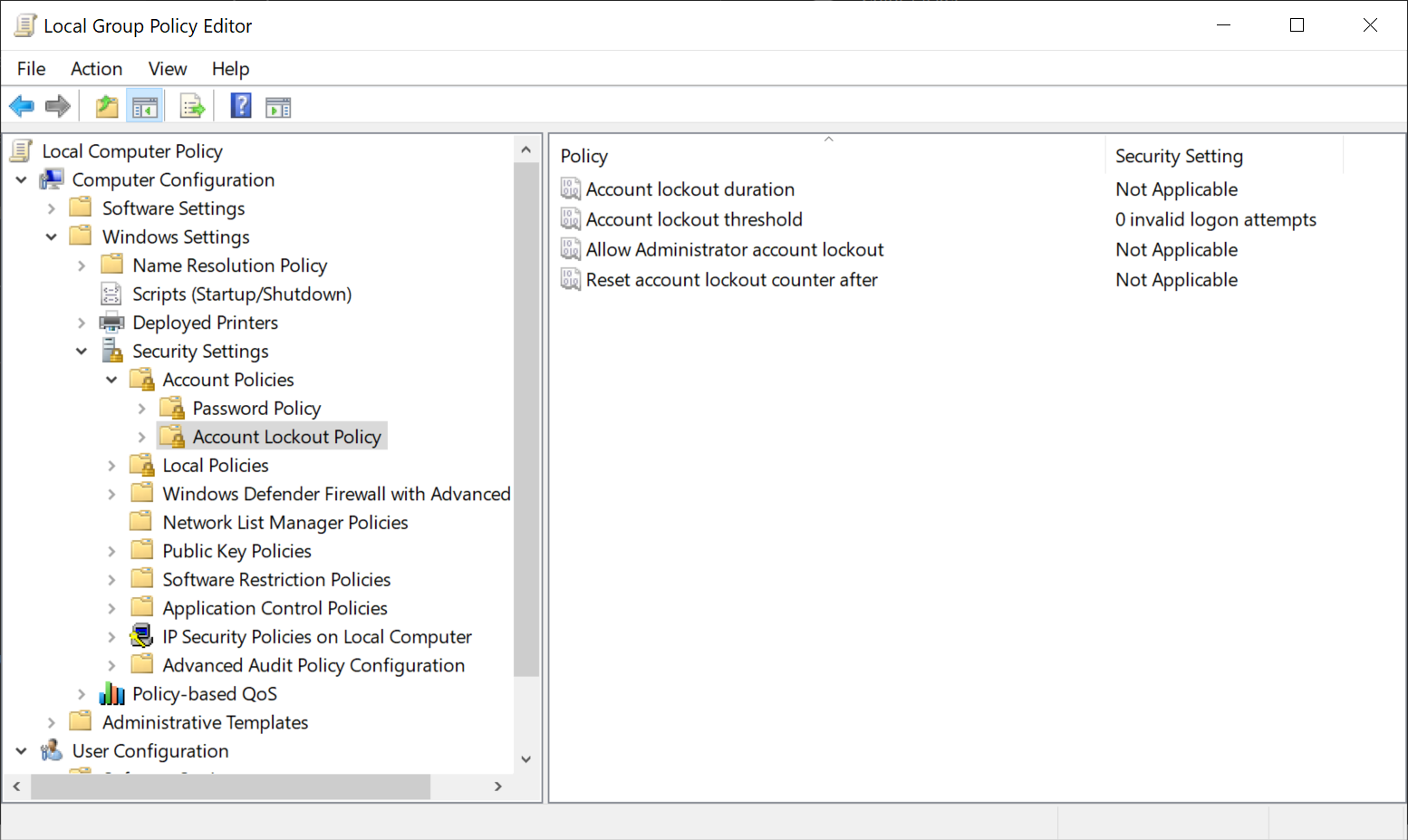
Account Lockout Policies
The following account local policies may be configured on any supported version of Windows, provided that the October 2022 security updates are installed on the device.
- Account lockout duration: determines the duration in minutes that a locked account remains locked before it is automatically unlocked. A duration of 0 keeps the account locked until an administrator unlocks it manually.
- Account lockout threshold: determines the number of failed login attempts required before an account gets locked automatically. A value of 0 disables the automatic lockout protection.
- Allow Administrator account lockout: determines whether administrator accounts may be locked out if too many invalid login attempts are recorded by the system.
- Reset account lockout counter after: determines the number of minutes that need to pass before the account lock counter is reset to 0.
Here is how these policies are configured or disabled, depending on whether they are active by default or not.
- Select Start, type gpedit.msc and select the Group Policy editor result.
- Go to Local Computer Policy > Computer Configuration > Windows Settings > Security Settings > Account Policies > Account Lockout Policy
- There you find all four policies.
- Double-click on a policy to configure it. All that is required is to change the default values to either enable it or disable it.
A restart of the PC is required to apply the changes.
Closing words
Some systems benefit from local brute force protections, especially if they are accessible by others. It is easy enough to configure the protections on older versions of Windows to reduce the chance of successful brute force attacks.
Now You: how do you protect your devices?
Thank you for being a Ghacks reader. The post Microsoft brings account brute-force protections to older versions of Windows appeared first on gHacks Technology News.


0 Commentaires