Google’s in-house Threat Analysis Group has recently uncovered an exploit framework that takes advantage of vulnerabilities in web browsers and other system utilities. TAG has also linked the exploit framework to a Spanish software company based in Barcelona. The exploit framework is known to target vulnerabilities in Microsoft Defender, Google Chrome, and Mozilla Firefox.
TAG is primarily one of Google’s expert-led lines of defense against state-sponsored attacks. However, TAG also keeps tabs on companies that let governments spy on political and moral opponents, dissidents, and journalists using tools of the surveillance trade. Officially, the Barcelona-based company claims to be nothing more than a custom security solution provider. However, the truth seems to be much more sinister. According to Google, this Spanish software company is one such commercial vendor of surveillance.
‘Continuing this work, today, we're sharing findings on an exploitation framework with likely ties to Variston IT, a company in Barcelona, Spain that claims to be a provider of custom security solutions.’
These are the sentiments of TAG’s Benoit Sevens and Clement Lecigne who recently addressed the team’s findings. TAG also stated that ‘Their Heliconia framework exploits n-day vulnerabilities in Chrome, Firefox and Microsoft Defender and provides all the tools necessary to deploy a payload to a target device.’
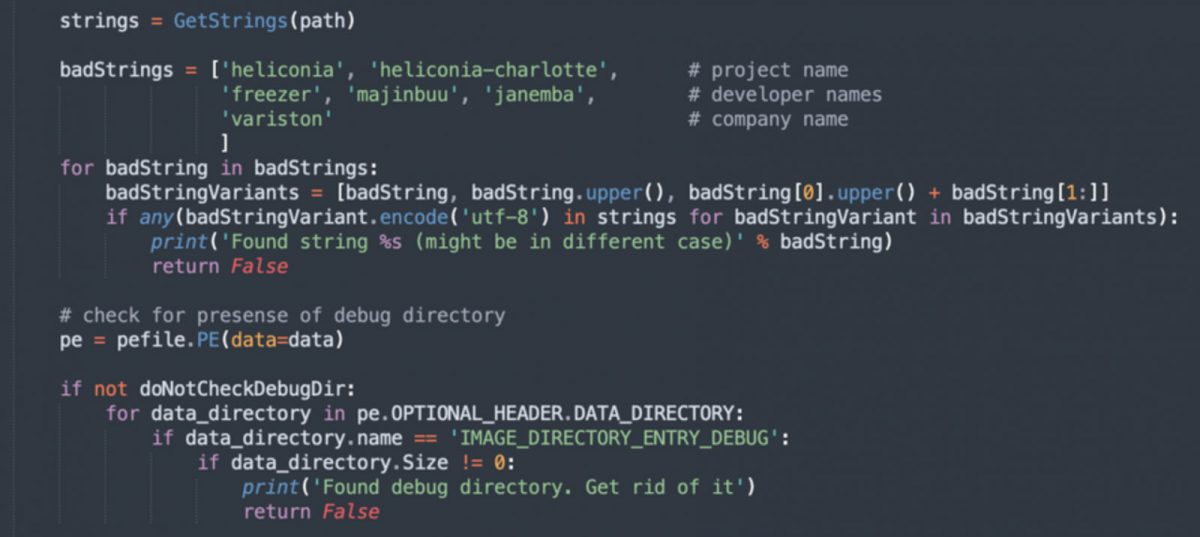
As TAG found, the exploit framework has three main components:
- Heliconia Noise: A Web framework that deploys renderer bug exploits. The framework then installs malevolent agents on the target system by deploying a Chrome sandbox escape.
- Heliconia Soft: A second web framework that carries a PDF payload that contains the Windows Defender exploit currently tracked as CVE-2021-42298.
- Heliconia Files: A set of exploits for Windows and Linux that target Firefox. One of these is currently being tracked as CVE-2022-26485.
Yesterday, TAG stated that The growth of the spyware industry puts users at risk and makes the Internet less safe, and while surveillance technology may be legal under national or international laws; they are often used in harmful ways to conduct digital espionage against a range of groups. These abuses represent a serious risk to online safety, which is why Google and TAG will continue to take action against, and publish research about, the commercial spyware industry.’
In other related news, Google is apparently developing tech to replace internet cookies.
Thank you for being a Ghacks reader. The post Google discovers a Windows exploit that points to distribution of spyware appeared first on gHacks Technology News.

0 Commentaires