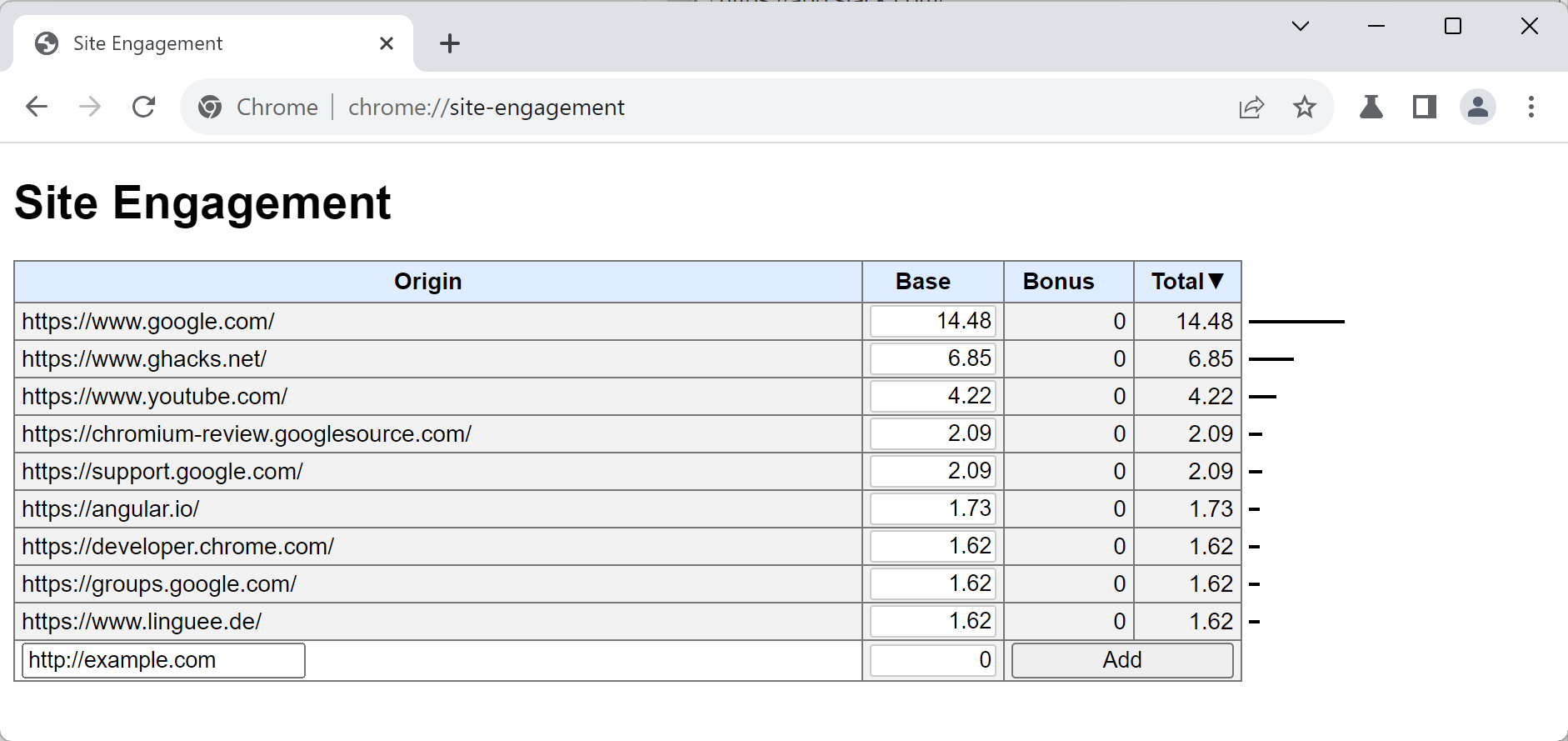
Google Chrome and all other Chromium-based web browsers collect site engagement statistics. It measures how "engaged" a user is with a particular site. The score ranges from 0 to 100, with 100 being "super engaged" and 0 not at all.
The browser uses signals to compute the score. Signals may include clicking and scrolling, keypresses, media playback, or direct navigations.
All users of Chromium-based browsers can open the information for their browser profile. Just load chrome://site-engagement/ in the browser's address bar to look at the list.
Google notes that the data is not synced, which means that it is device and profile specific. Site engagement may be used by the browser, e.g., to prioritize tab discarding or allowing/blocking certain invasive features.
The information is copied whenever an Incognito session is opened in the browser, but no information is written back. This information is deleted when the browser is shut down according to the official documentation.
Your browser may leak your frequently visited websites
Site engagement information may leak to visited websites, according to a report on the Fingerprint website, at least in Google Chrome. A demo page is available for Google Chrome.
The researchers use another Chrome feature, Lookalike Warnings, for that. Lookalike Warnings is a security feature that uses heuristics to determine if the user meant to visit a different website. A common example is a typo in the domain name, e.g., gooogle.com instead of google.com.
Lookalike Warnings is designed to warn users if it believes the site may not be the intended target and give them the chance to open the right website. Google Chrome uses a list of 4990 popular domains for that according to Fingerprint.
To find out if a user's engagement with a site is high, websites can try to load "lookalike" domains. Martin Bajanik over at Fingerprint explains: "Any website can initiate navigation by opening a new browser window with the detection website. This action requires user interaction, such as clicking a button; otherwise, the browser will block the popup window. However, a single popup window can be reused to test multiple websites, as the opener can repeatedly redirect the popup window to different locations."
What websites do with the information is up to them. From displaying targeted advertisement to malicious activities, all is possible.
Deleting site engagement
There is no option to disable site engagement in Chromium-based browsers. All collect the data and all provide access to the information to users.
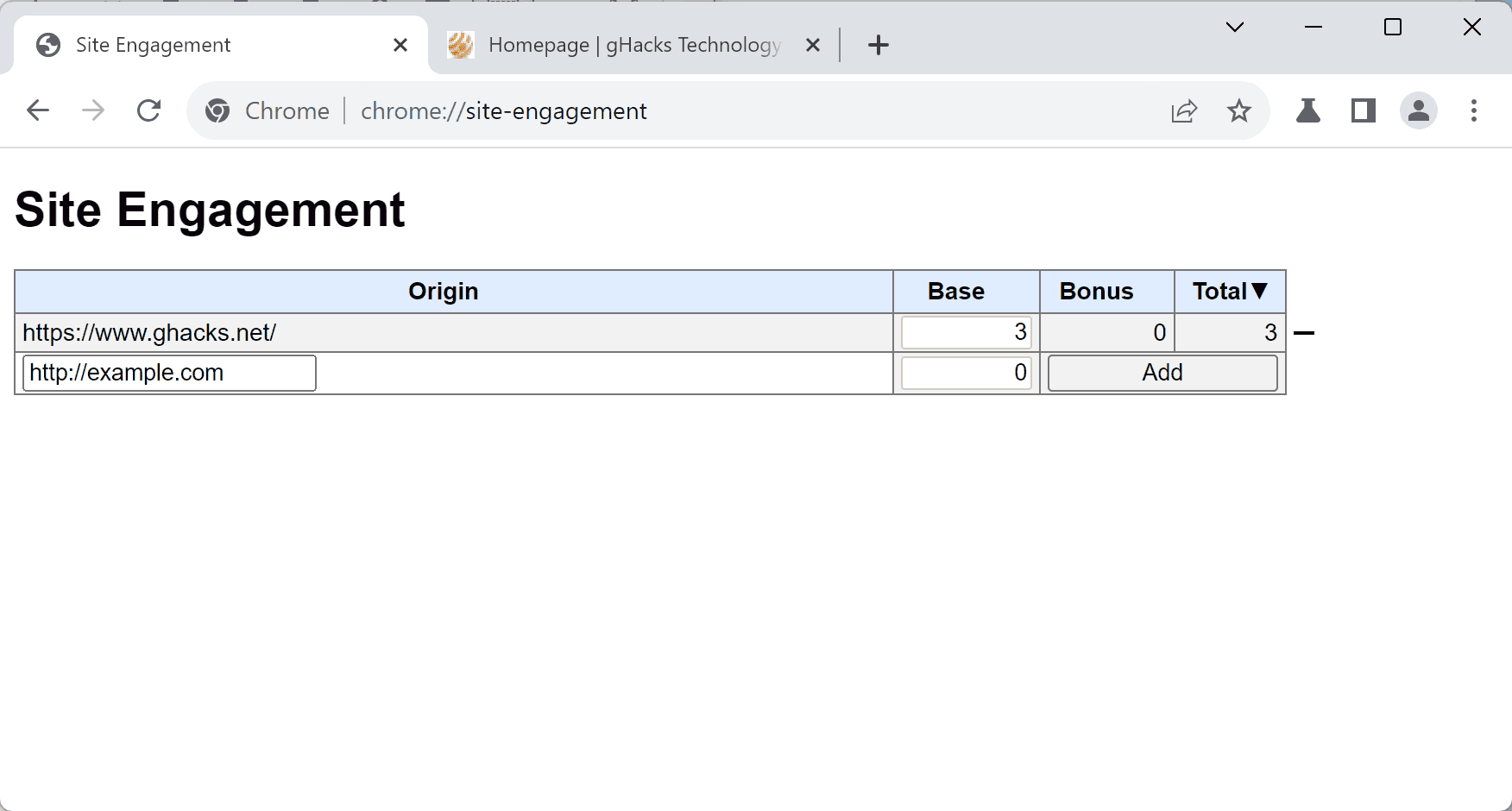
Since there is no way to disable the collection, the next best thing is to delete the data regularly. The Chromium documentation reveals that engagement scores are linked to the browsing history. In other words, when users delete the browsing history, engagement scores are cleared.
Chrome users may load chrome://settings/clearBrowserData in the browser's address bar to open the Clear Browsing Data menu.
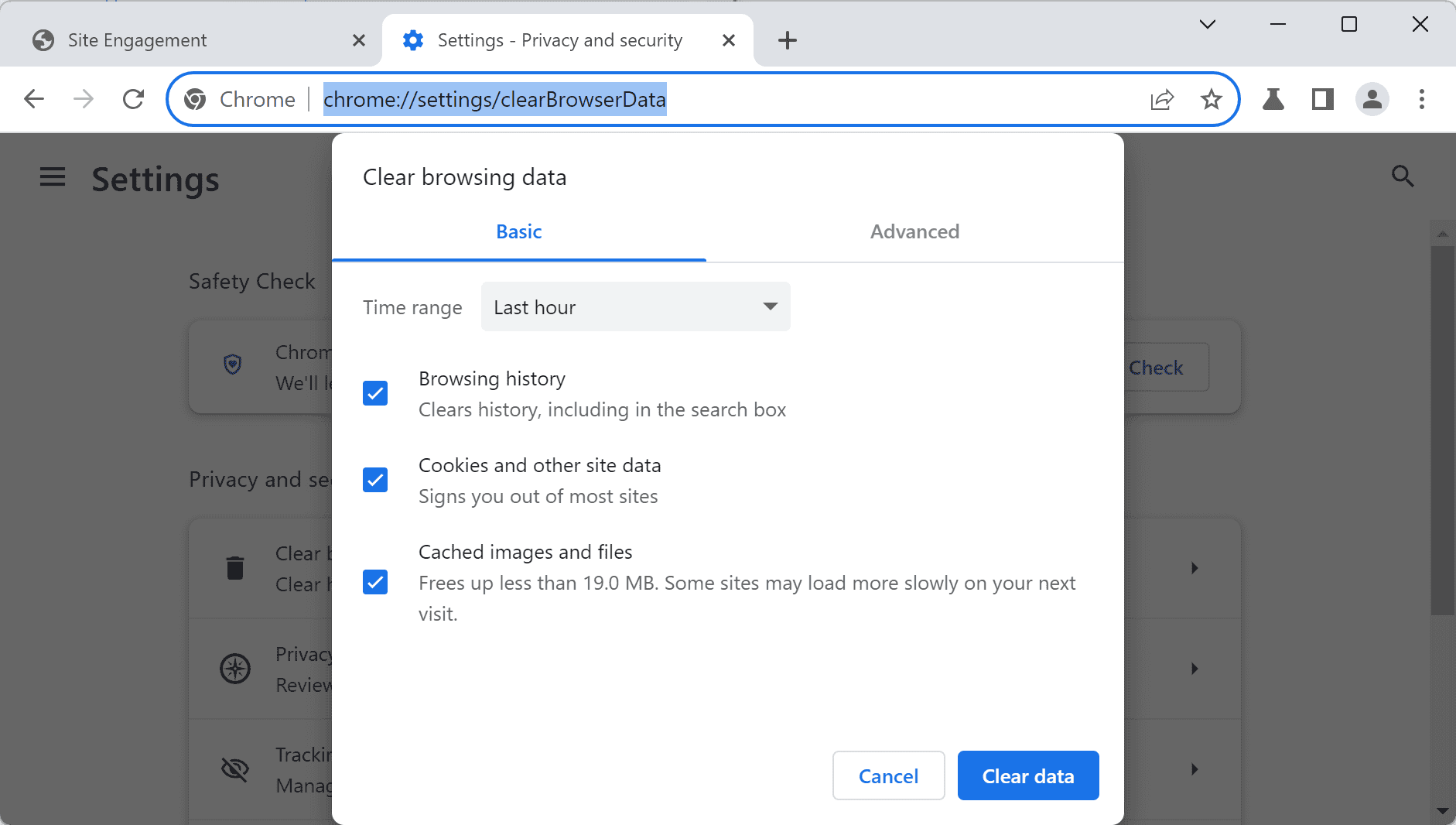
To clear the entire browsing history, select "all time" in the time range menu and make sure that browsing history is checked. Note that clearing the browsing history may temporarily interfere with certain browser features.
Restart the web browser and check the site engagement page again. It should list only a demo site and nothing else.
Closing Words
While this won't be used for widespread attacks or tracking, it is interesting nevertheless that something like this is possible. Switching to another Chromium-based browser, or better a non-Chromium-based browser, resolves this particular issue.
Now You: what is your take on this privacy issue?
Thank you for being a Ghacks reader. The post Report: This Chrome feature may leak frequently visited sites appeared first on gHacks Technology News.

0 Commentaires