Microsoft published information about a new malware on its security website on April 12, 2022. The malware, named Tarrask, exploits a bug in Windows' task scheduling system to evade detection.
Tarrask is used by the hacking group Hafnium, which targeted telecommunication, Internet Service Providers and the data services sector in the past.
The group uses zero-day vulnerabilities for its attacks to get into computer systems. Once a system has been attacked successfully, a bug in Windows is used to hide traces of the malware and make detection harder. Tarrask uses the bug to create scheduled tasks that are hidden to avoid detection and likely also for persistency.
The Windows Task Scheduler is used by the system and by applications to launch tasks, e.g., to check for updates or run maintenance operations. Applications may add tasks to the Task Scheduler, provided that they are executed with sufficient rights to do so. Malware uses tasks often, according to Microsoft, to "maintain persistence within a Windows environment".
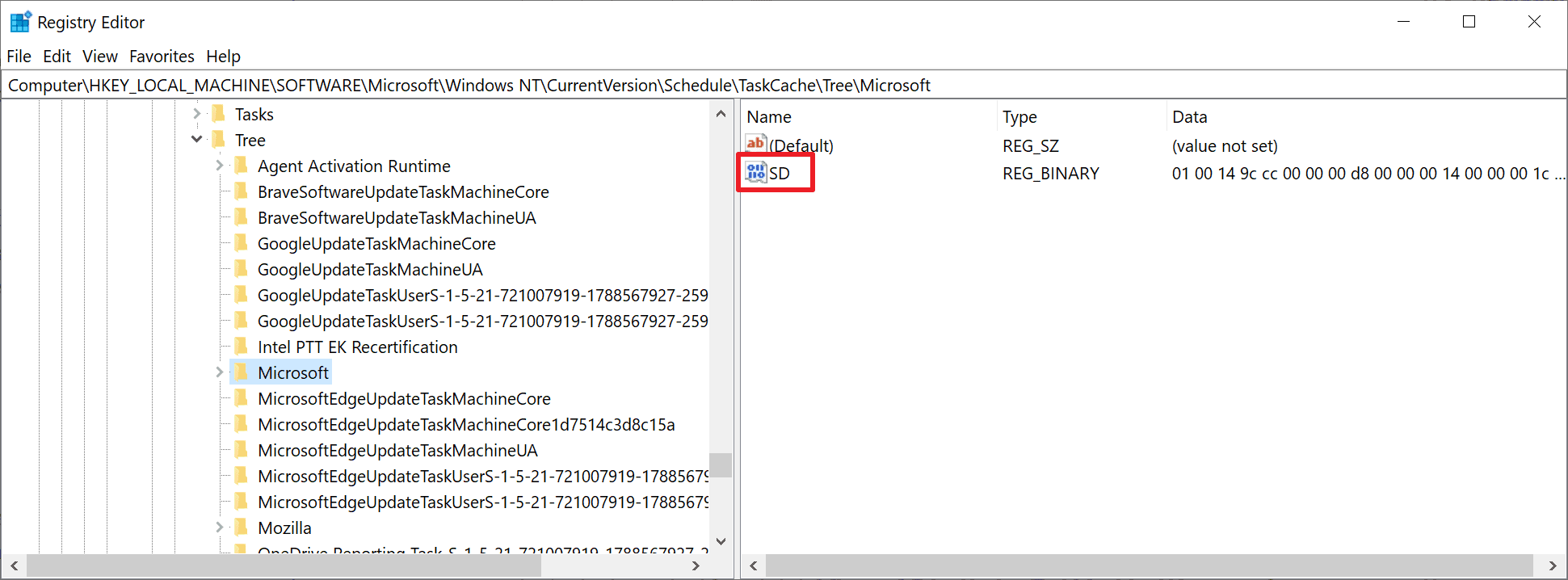
Tasks may be analyzed by launching the Task Scheduler tool on Windows. Tarrask uses a bug to hide its task from the tool and also the command line option "schtasks /query", which returns a list of scheduled tasks that exist. To avoid detection, Tarrask deletes the Security Descriptor value of the task in the Windows Registry; this results in the task's disappearance from the Task Scheduler and from the command line tool. In other words: careful inspection of all tasks using either of the tools won't reveal the malicious tasks.
Detecting Tarrask on Windows systems
The malware does not remove task information entirely, as traces of it are still recorded in the system Registry. Microsoft suspects that the hacking group left the data in the Registry to make the malware persistent, or, that the group was unaware that the task would "continue to run" after removal of the SD component.
Windows administrators may analyze the scheduled task information in the system Registry to find out if a system is infected with the Tarrask malware:
- Use the keyboard shortcut Windows-R to display the run box.
- Type regedit.exe and hit the Enter-key.
- Navigate to the path HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\. You get the list of scheduled tasks that exist on the system.
- Go through each task to determine if one is listed without SD value.
If a task without SD value is found, it is a hidden task that is not displayed in the Task Scheduler or the command line utility. The task can't be deleted normally, as it is running within the context of the SYSTEM user. Attempts to delete the task will fail with an access denied error message.
The last version of Microsoft's Windows Defender security application detects the malware. Microsoft added a new observation event to Windows Defender that detects hidden tasks; these are flagged as Behavior:Win32/ScheduledTaskHide.A then by the application.
Microsoft recommends that system administrators adopt the following recommendations and security guidelines to detect malware that is using the attack vector:
Enumerate your Windows environment registry hives looking in the HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree registry hive and identify any scheduled tasks without SD (security descriptor) Value within the Task Key. Perform analysis on these tasks as needed.
Modify your audit policy to identify Scheduled Tasks actions by enabling logging “TaskOperational” within Microsoft-Windows-TaskScheduler/Operational. Apply the recommended Microsoft audit policy settings suitable to your environment.
Enable and centralize the following Task Scheduler logs. Even if the tasks are ‘hidden’, these logs track key events relating to them that could lead you to discovering a well-hidden persistence mechanism
Event ID 4698 within the Security.evtx log
Microsoft-Windows-TaskScheduler/Operational.evtx logThe threat actors in this campaign used hidden scheduled tasks to maintain access to critical assets exposed to the internet by regularly re-establishing outbound communications with C&C infrastructure. Remain vigilant and monitor uncommon behavior of your outbound communications by ensuring that monitoring and alerting for these connections from these critical Tier 0 and Tier 1 assets is in place.
Other malware may exploit the bug as well to avoid detection.
Now You: which security software do you use?
Thank you for being a Ghacks reader. The post How to detect the Windows Tarrask Malware that uses a bug to avoid detection appeared first on gHacks Technology News.
0 Commentaires